Loupe Active Directory Integration: More than Just Logging in
Like most applications, Loupe Server has its own database of users. For many organizations this is a perfectly reasonable approach to authorization and authentication. Recently, with Loupe Enterprise rolling out to more and more organizations, we’ve gotten some strong feedback that we needed to support Microsoft Active Directory. In particular:
- Larger organization require authentication go back to a single directory to ensure there’s just one place to enable users and grant them access.
- As a shared resource, multiple teams work with Loupe Server. Central IT doesn’t want to have custom administration procedures and no one team wants to have the burden of managing a shared service.
We’ve hit both of these with the new Active Directory integration in Loupe 3.7.
Working with Active Directories
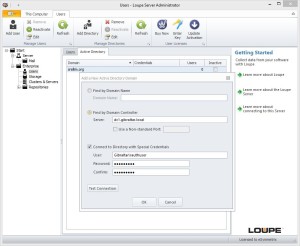
Multiple domains can be added to a Loupe Server installation. These might be local domains (where the Loupe Server is a member of the domain and you can resolve the domain controllers through DNS) or remote domains where you need to specify a domain server and credentials of an account in that domain. Once you’ve established a link with a domain controller it’s available for creating users.
When a user is created from an Active Directory their display caption, user name, and email address are automatically kept in sync with their AD user. This works even if the user name is changed since the internal GUID of the AD user is carried across into Loupe.
If an AD user is disabled, expired, or locked out they won’t be able to log into Loupe Server. Whenever they go to log in, the validation of their username & password are delegated down to AD and it get the final say; the password is never stored in Loupe.
Automating User Management
To eliminate manual administration Loupe Repository now provides User Management Rules. Each rule designates an Active Directory Group and a user role within Loupe for members of that group. In the background, Loupe automatically scans the list of rules for each repository and determines the highest level of access it should grant each user that is part of a rule.
In addition to creating users, each repository can be constrained to only support AD users (whether created by a user or manually) and can be set to only allow AD users from a rule. By setting both these options, users will be automatically created as they are added to an AD group and will be deleted if they are disabled or no longer a member of a suitable group.
Put it all together and what does it mean?
- Map a few groups you likely already have into Loupe and you never have to worry about administering security within Loupe again.
- Different teams can have different rules for their own repositories.
No Messing Around with Config Files
 A major customer of ours let us in on a secret recently - what had Loupe “make the cut” when they started evaluating products was we provide a complete GUI for configuration. No messing around with finding the exact version of Java, installing Tomcat, or editing a big xml or JSON file - just run the install and answer the questions in the GUI.
A major customer of ours let us in on a secret recently - what had Loupe “make the cut” when they started evaluating products was we provide a complete GUI for configuration. No messing around with finding the exact version of Java, installing Tomcat, or editing a big xml or JSON file - just run the install and answer the questions in the GUI.
In that same spirit, we’ve made sure to put everything you need to manage AD integration right in the Loupe Server Administration GUI. This includes automatically testing the configuration and previewing for you what you’ll get if you change a user management rule. We know you’ve got a whole job to tackle - the last thing you want to do is learn the ins and outs of a new command file syntax!
Sounds Sweet, How do I Use This?
Active Directory integration is available in Loupe Enterprise Edition and to Loupe Enterprise Subscriptions. It’s configured using Loupe Server Administrator, so if you have your own installation RDP into a cluster server to set it up. For Subscription customers, contact us through support to do the integration. We’ll need access from our central infrastructure to one of your AD servers and credentials for an account to use for the integration.